APWG Applied Research
Counter-Cybercrime Innovation in the Public Interest - Since 2003

APWG’s research and development programs establish data assets, metrics, and conventions that are deployed as permanent working counter-cybercrime resources, such as the APWG eCrime eXchange cybercrime event data clearinghouse; the education-page redirect program, and the STOP. THINK. CONNECT. cybersecurity awareness campaign.
The criterion by which APWG’s R&D programs are prioritized is their potential scale for suppressing the cybercrimes against which they are targeted
The APWG’s initial phishing URL repository was architected in Fall 2003 by Internet infrastructure managers, major bank security teams and security product developers – and deployed within months. Its antecedents are still operating to this day as components of the APWG eCrime eXchange, APWG’s cybercrime data clearinghouse, delivering billions of data elements to APWG members and helping to secure billions of devices and software clients.
Likewise, APWG’s Phishing Education Landing Page was conceived by Reseachers from Carnegie-Melon University presenting at the APWG 2007 eCrime Conference, for instance. The landing page was operational within a few months, now educating each month hundreds of thousands of credulous users who click on links to decommissioned phishing websites – and responding to them in some 21 languages.
APWG’s proposal for a messaging convention of commercial enterprises and governments sharing a common cybersecurity campaign of shared media assets, was first proffered to its members in winter of 2008. That proposal inspired and informed the development of the STOP. THINK. CONNECT. campaign and its adoption by the US Government in 2010. The campaign has subsequently been launched in 22 other nations. Meanwhile, dozens of other national ministries and NGOs, in addition, have signed the Messaging Convention’s memorandum of cooperation in preparation for their own campaign launches.
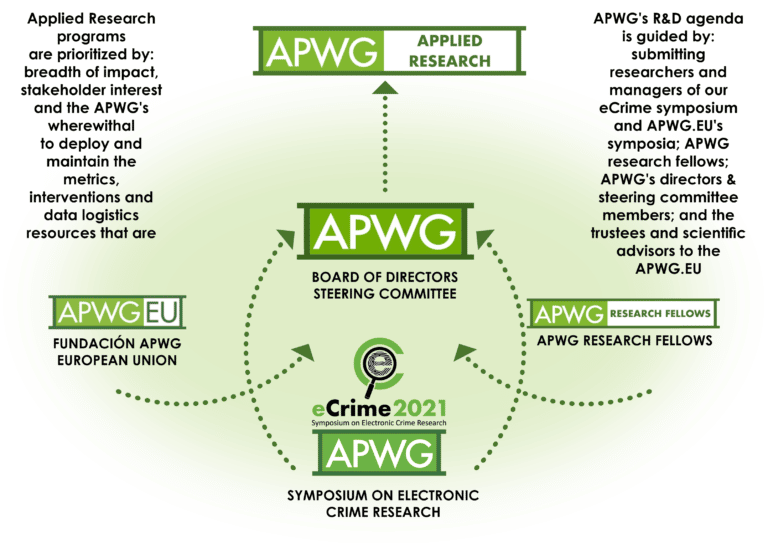
The applied research projects that APWG has completed and currently curates have often been provoked by research presented at the annual APWG Symposium on Electronic Crime Research, almost since the conference’s founding in 2006.
APWG’s applied research programs have also, however, reflected a broad mix of the interests of its members, the research community that coalesced around the eCrime conference, as well the law enforcement community and civil society and intergovernmental organizations with which the APWG is regularly correspondent.
Those programs have fallen broadly into three topical research topic sections: data logistics and telemetry; behavioral and neurocognitive dimensions of cybercrime victimization; and industrial and public policy aspects of cybercrime management.
PROGRAMS IN DEVELOPMENT AT APWG APPLIED RESEARCH SECRETARIAT
PhishFarm: Block List Latency Monitoring
The APWG PhishFarm Block List Latency Monitoring Program would provide insights into the browser block lists that are one of the last lines of defense between workaday users and phishing websites — an enterprise that is essential to understanding the efficiency of the cybercrime response ecosystem. Operationally, we’ll be building a latency measurement scheme into the APWG eCrime eXchange that provides insight into the time lag between submitting a URL to eCX and the moment the block lists begin actually blocking the URL – if at all.
With a reliable system for measuring the latency and efficacy of block list updating stakeholders will have foundational metrics required for:
* Measurement of blocklist report instantiation efficiency
* Development of optimization schemes and policies for phishing URL reporting
* Discovery of sophisticated, high-impact attacks
* Measurement of mitigation efficacy
* Whole ecosystem performance assessment.
National Cyber Resilience Baselining
The APWG is working with research centers in Australia, and the United States to deploy the world’s first national base-lining survey of user resilience to the common cybercrime of phishing to gain insights into behavioral aspects of phishing – and to establish data corpora for university and industry investigators researching the behavioral/cognitive dimensions of cybercrime.

Principle investigators from La Trobe University and Indiana University are organizing this program to engage user behavior in cyber security as a public health problem, adapting techniques from epidemiology to generate data that is representative of the whole population – not a biased sub-sample. The data generated from this study will help to extend the field, but more importantly, will be shared with system designers to help build more secure tools and better incident response capability.
This study will extend an existing instrument developed at Indiana University that measures responses to simulated phishing attacks, and deliver it to a target 9,798 randomly sampled users nationally (approximately 0.2% of the population). This sample size has been selected because it is the minimum sample size required to achieve a Confidence Level of 0.99, with a Confidence Interval of 0.5, given a population of 24,511,800 in Australia.
Meanwhile. APWG is working with principal investigators in a number of European countries to consider the potential for deploying baselining studies of their nations’ populations as well.
Crypto Currency Wallet Address Data Corpus
In 2018, the APWG inaugurated the APWG Crypto Currency Working Group (CCWG) to help cryptocurrency exchanges, wallet hosters, trading platforms and investment funds protect themselves and their customers against phishing and cybercrime – and established a data endpoint on the APWG’s eCrime eXchange (eCX) for wallet addresses associated with cybercrime events.
Today, the CCWG’s /crypto API endpoint on the APWG’s eCrime eXchange is delivering hundreds of millions of data entities per month outbound to its members, providing event records in a complete and verbose schema that provides key primary wallet address data for those payment instruments suspected of providing cash out mechanisms for scams and racketeering operations.
In development of the CCWG’s data corpus of wallet addresses, the APWG has turned to the research community that has formed up around the APWG’s Symposium on Electronic Crime Research (APWG eCrime) to mine for fresh insight into cybercrime’s unique challenges and for opportunities in sourcing event data for the CCWG.DB. Actively updated data is drawn from a number of online resources and experimental platforms – including, for example, a University of Ottawa recruitment platform that isolates bitcoin generator scams and writes the cash-out wallet addresses to the CCWG.DB.





